I’ve already written quite a bit about getting on the wire as it pertains to packet analysis. Half the battle when you are capturing packets is placing the sniffer computer so that it captures the packets you need. The advent of switched networks makes this a bit harder on us as traffic is now directed and not free-flowing across every port on a network. In a post a few months ago I outlined three methods for getting on the wire. Those three methods were ARP Cache Poisoning, Hubbing Out, and Port Mirroring. One other technique which I had not previously used, but have now grown to love is using a network tap.
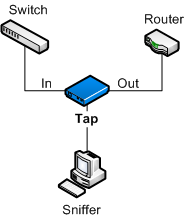 A tap is basically a hardware device that you can place on the wire to intercept the right packets.
A tap is basically a hardware device that you can place on the wire to intercept the right packets.
The tap has at least three ports. These are inbound and outbound ports and a monitor port.
Say you wanted to intercept all network traffic entering your router. Typically, you would have a single cable going from a switch to your router. In order to insert the tap into the mix, you would unplug the current cable from the router and plug it into the inbound port on the tap. You would add an additional cable from the outbound port of the tap into the port on your router. Lastly, you would place a cable into the monitor port that leads to your analysis machine. The analysis machine will then capture all traffic flowing between the switch port and the router.
The great thing about doing this as opposed to hubbing out is that you aren’t using an old school hub that could cause dropped packets and limits you to half-duplex communication. This is also advantageous over ARP cache poisoning because it doesn’t generate any extra traffic on the wire, which is something you typically want to avoid doing…especially in security scenarios. If your layer three switches typically have a very high processor utilization, you could also consider this over port mirroring. The tap adds no extra traffic or latency to the traffic on the wire and is completely undetectable.
 That all being said I recommend the Barracuda network tap. They run about $130 and have an added benefit of having TWO monitor ports. One port monitors all inbound traffic and the other monitors all outbound traffic rather than having a single port for both, which can add some flexibility in your analysis. The Barracuda tap also allows for the use of a nine volt battery in situations where a power outlet isn’t handy or you just want to capture some packets quickly.
That all being said I recommend the Barracuda network tap. They run about $130 and have an added benefit of having TWO monitor ports. One port monitors all inbound traffic and the other monitors all outbound traffic rather than having a single port for both, which can add some flexibility in your analysis. The Barracuda tap also allows for the use of a nine volt battery in situations where a power outlet isn’t handy or you just want to capture some packets quickly.
You can get the Barracuda network tap from http://www.barracudanetworks.com/tap/.
Great article!
Should I be using regular patch cable or will there be occasions when I need a cross-over cable?