In September of this year, I successfully defended my doctoral dissertation, earning the title of…
Category: Publications
I’m thrilled to announce the release of my newest book, Intrusion Detection Honeypots: Detection through…
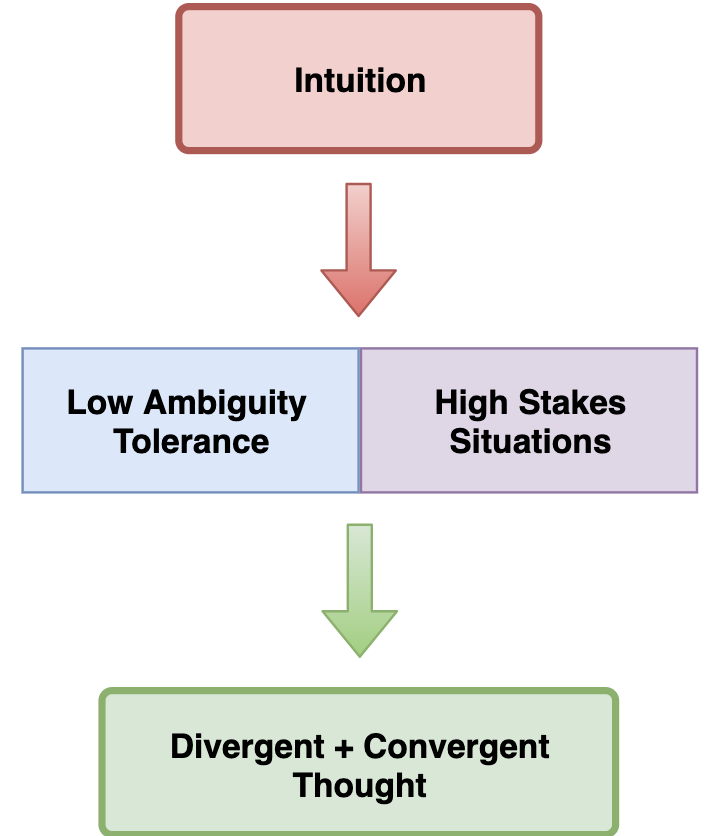
Creative Choices: Developing a Theory of Divergence, Convergence, and Intuition in Security Analysts
Humans lie at the heart of security investigations, but there is an insufficient amount of…
Since the latest edition of Practical Packet Analysis has been released, so many people have been…
A few weeks ago on Twitter, I teased that I was working on a new…
Ten years after releasing the first edition of Practical Packet Analysis, the third edition is…
If you like the content on my blog, one of my presentations, or enjoyed any…
All of the royalties from Practical Packet Analysis and Applied NSM are donated to public school…
I recently had the opportunity and pleasure to speak at MIRCon 2014. The topic of…
I recently gave a presentation at BSides Augusta on the topic “Defeating Cognitive Bias and…