My name is Chris Sanders, and I’m a security analyst.
When I first started out, learning how to investigate threats was challenging because there was no formal training available. Even in modern security teams today, most training is centered around specific tools and centers too much around on the job training. It wasn’t hard to learn how to use the tools, but I struggled knowing when to use them and what to look for. It wasn’t that I didn’t have enough data…I was overwhelmed by it.
My investigations all followed a similar path.
After getting an alert I’d look in the obvious places — my go to’s that I would later realize were crutches:
- Pull the packet capture
- Look at the HTTP requests
- Google the alert name to find more context
….but then I’d get overwhelmed.
“What data sources are available?”
“Can I find the host logs based on what information I already have?”
“Is this normal? How can I tell?”
Worse yet, if I did find something interesting I was completely unorganized. I had a dozen browser tabs open, data spread across four terminal windows, and nonsensical notes that I’d wrote 5 minutes earlier and had already forgotten the meaning of.
I was paralyzed.
The longer this went on the more I became overwhelmed. I would eventually just stare at the screen hoping for a sudden moment of clarity and for everything to just click. It never happened.
What was I lacking? I knew plenty of people who were good at this — what skill did they possess that I did not?
I sought out a colleague I knew who is an experienced analyst at a big government agency. He was one of the most skilled members of their threat hunting team and spent his time tracking down nation-state level adversaries. I asked him how he learned to be a good analyst, and he told me, “Chris, being a good analyst isn’t really something you can learn. You’ve either got it, or you don’t. You can’t teach this stuff.”
I call malarky.
After I recoiled from the wave of smugness that had suddenly washed over me, I resolved to strive for something better. Chalking investigative ability exclusively up to natural born traits was an excuse, and I that way of thinking had led me to believe things that forced me to make my own excuses.
3 beliefs that were holding me back
This discussion was a critical moment in my career. It made me realize three ridiculous beliefs that were holding me back. When I figured this out, it changed the way I looked at everything.
I want to share them with you now.
Belief #1: You have to be born with some special sauce to be a good investigator.
WHAT I THOUGHT: Some people were born “naturals” or were simply much smarter than me.
MY EXCUSE: I’ll probably never figure this out because I’m simply not smart enough.
THE TRUTH: We all start in different places, but nearly anyone can achieve some level of success as a security analyst. Some people get it a little sooner than others and that naturally leads them to situations where they get more practice — more interesting data, a better job, etc. This accelerates their learning.
Belief 2: Being a great analyst is all about mastering your tools
WHAT I THOUGHT: I should spend most of my time learning tools. If I can write great Bro scripts or use IDA, then I’ll be able to find attackers on my network and see what they’re doing.
MY EXCUSE: I’m doing everything I can to learn the skills that are important for my job by focusing on the tools of the trade.
THE TRUTH: Knowing how to use your tools is helpful, but when and why to use them is critical. Tools do things like help us retrieve and manipulate data, but where most people get stuck is decided what data to query and how to manipulate it so that answers to important questions become clear.
Belief #3: Investigating security incidents is a completely new and unique concept
WHAT I THOUGHT: The skills involved in investigating alerts and threat hunting are entirely unique to our field.
MY EXCUSE: This knowledge is so specialized that only a small number of people will be able to really grasp it.
THE TRUTH: Investigating things isn’t unique to cybersecurity. Several fields involve some form of investigation — police officers, lawyers, and even doctors. We can leverage the knowledge of these fields and many more to become better blue teamers.
The problem of tacit knowledge
A major problem working in a new field is that much of the knowledge needed to perform the job is tacit — it isn’t written down. That’s why so much learning that happens on the job mostly focuses on just sitting and watching others do it. We can do better.
When security analysis finally began to “click” for me I resolved not just to be good at catching bad guys — I wanted to help others who are going down the same path by developing a course dedicated exclusively to both the theory and practice investigation process.
Introducing…

If you’re a security analyst responsible for investigating alerts, performing forensics, or responding to incidents then this is the course that will help you gain a deep understanding how to most effectively catch bad guys and kick them out of your network. Investigation Theory is designed to help you overcome the challenges commonly associated finding and catching bad guys.
- I’ve got so many alerts to investigate and I’m not sure how to get through them quickly.
- I keep getting overwhelmed by the amount of information I have to work with an investigation.
- I’m constantly running into dead ends and getting stuck. I’m afraid I’m missing something.
- I want to get started threat hunting, but I’m not sure how.
- I’m having trouble getting my management chain to understand why I need the tools I’m requesting to do my job better.
- Some people just seem to “get” security, but it just doesn’t seem to click for me.
Investigation Theory will teach you how to conduct investigations regardless of the toolset by focusing on the mental models used by experts.
Course Format
Investigation Theory is not like any online security training you’ve taken. It is modeled like a college course and consists of lectures, labs, and exercises where you’ll receive individualized feedback. The course is delivered on-demand so you can proceed through it at your convenience. However, it’s recommended that you take a standard 10-week completion path or an accelerated 5-week path. Either way, there are ten modules in total, and each module typically consists of the following components::
- Core Lectures: Theory and strategy are discussed in a series of video lectures. Each lecture builds on the previous one.
- Bonus Lectures: Standalone content to address specific topics for those who want to dive deeper into a topic or apply the material in unique ways
- Reading Recommendation: While not meant to be read on pace with the course, I’ve provided a curated reading list along with critical questions to consider to help develop your analyst mindset.
- Formative Exercises: You’ll participate in unique exercises that allow you to apply what you’ve learned and make it useful to you. By approaching concepts from multiple different perspectives, you’ll better retain and apply what you’re learning. I’ll also provide you with feedback from to help coach you along the way.
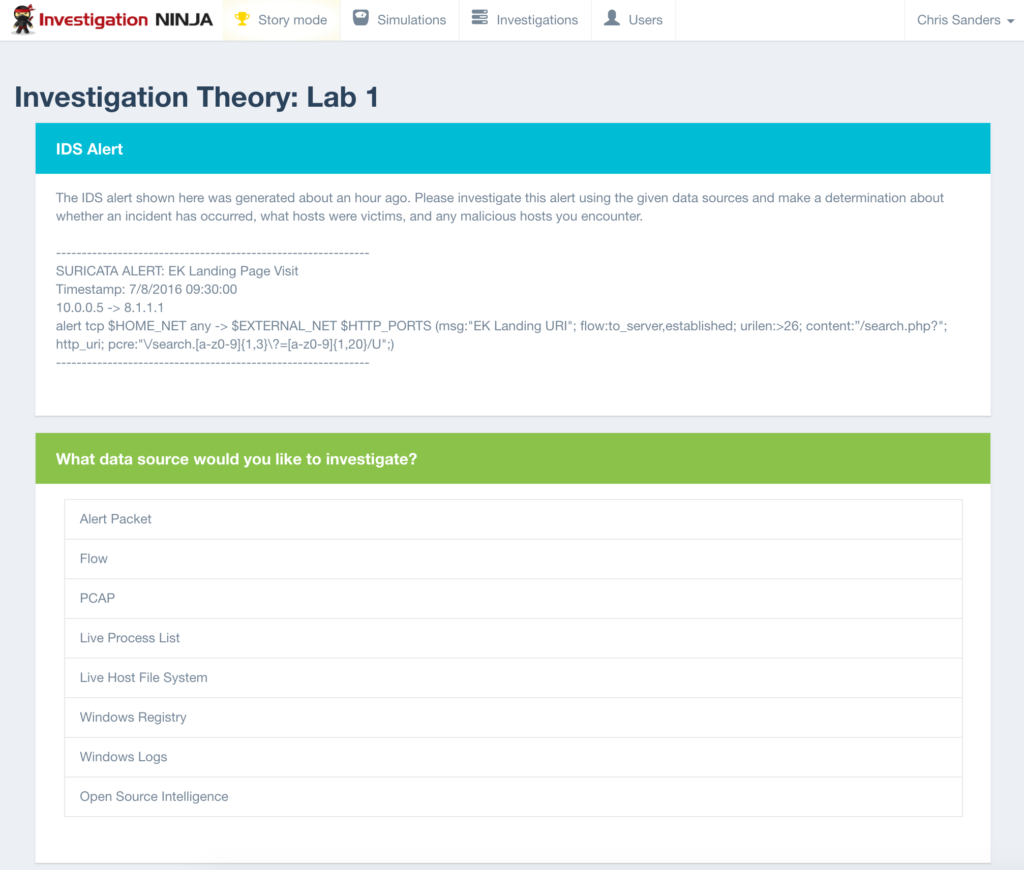
- Lab Exercises: The Investigation Ninja system is used to provide labs that simulate real investigations for you to practice your skills.
Investigation Ninja Lab Environment
Investigation Theory utilizes the Investigation Ninja web application to simulate real investigation scenarios. By taking a vendor agnostic approach, Investigation Ninja provides real-world inputs and allows you to query various data sources to uncover evil and decide if an incident has occurred, and what happened. You’ll look through real data and solve unique challenges that will test your newly learned investigation skills. A custom set of labs have been developed specifically for this course. No matter what toolset you use in your SOC, Investigation Ninja will prepare you to excel in investigations using a data-driven approach.
Get stuck in a lab? I’m just an e-mail away and can help point you in the right direction.
Evidence Overview Lessons
Expert analysts are skilled at collecting and manipulating diverse forms of digital evidence. In Investigation Theory, I provide a framework that will help you more quickly understand the capabilities of interpretation of evidence to accelerate how you gain experience in this area. Along with that framework, I created several evidence overview lessons that provide an introduction to the most common data sources from an analysts perspective. For each evidence source you’ll learn which investigative questions it can be used to answer, how to interpret it, and see demos of common collection and analysis tools. I’ll also provide a deliberate practice plans that you can use to continue experimenting with common evidence sources. These evidence overview lessons include topic areas such as Windows event logs, flow records, web proxy logs, email transaction logs, and more.
Instructor Q&A
This isn’t a typical online course where we just give you a bunch of videos and you’re on your own. The results of your progress, quizzes, and labs are reviewed by me and I provide real-time feedback as you progress. I’m available as a resource to answer questions throughout the course.
Syllabus
- The Investigation Process: Diagnostic Inquiry — The first lesson will introduce the concepts we’ll use to develop your analysis skills. I’ll describe our first two mental models, the attack timeline and the diagnostic inquiry model of investigations. These models will define how you approach and utilize evidence and represent attacks. You’ll also learn about the power of metacognition.
- Evidence: Knowing Where to Look When You Hear Hoofbeats — Before you can ask the right questions, you must understand the realm of possibilities represented by available evidence. I’ll describe mental models for organizing evidence and understanding the nuance inherent to using it. I’ll also provide frameworks for documenting and learning about your evidence.
- Questions: A Question Well Stated is a Problem Half-Solved — The thing that sets expert analysts apart more than anything else is the ability to ask the right question at the right time. This lesson will describe several mental models and techniques asking better investigative questions.
- Decisions: Making Meaning from Data — Analysts thrive on the ability to derive meaning from evidence. In this lesson, you’ll learn different techniques for finding meaning in data and how your observations represent cues that lead to decisions.
- Transforming Data: Finding Answers in Evidence — Even if you know where to look, many of the answers you seek won’t just jump right out at you. This lesson will describe the techniques used to investigate evidence: graphs, aggregations, pivots, statistics, and search.
- Investigation Playbooks: How to Use Inductive Reasoning to Predict Questions and Gain Efficiency — Some of the investigation inputs you’ll encounter will lend themselves to predictable questions. These make up the basis for playbooks. This lesson will show you how to create simple, but effective investigation playbooks building on what you’ve learned so far.
- Threat and Open Source Intel: Understanding the Unknown — You must be able to leverage collective intelligence to understand the context of the events you investigate. This lesson provides a framework for pursuing open source intelligence data for researching external threats.
- The Curious Hunter: Finding Investigation Leads without Alerts — Threat hunting is a form of investigation where the responsibility of finding the initial detection lead falls on the human analyst. This lesson introduces two mental models for practically approaching hunting, how to develop hunting skills, and pitfalls associated with these investigations.
- Your Own Worst Enemy: Recognizing and Limiting Bias — Bias is inherent to the human condition and it is both a good and bad thing. This lesson discusses the nature of bias and the numerous ways it can affect your investigations. I’ll also describe mental models for helping identify and diminish the negative affects of bias.
- Reporting: Effective Communication of Breaches and False Alarms — Your investigative work doesn’t matter if you can’t effective express your findings. This lesson will teach you how to use storytelling to better express your findings and provides metrics for measuring investigation success
Plus, several bonus lectures on topics like alert triage strategy, specific analytic techniques, and the concept of “mise en place” to master your analysis environment!
You can view the detailed course syllabus here.
Investigation Theory includes:
- Over 30 hours of demonstration videos. These videos will provide the theoretical foundations of the investigation process, mental models for effective investigations, and SOC best practices to tie these to your workflow.
- Hands-on labs to help you develop and test your skills. You’ll complete lab exercises in the Investigation Ninja tool. Review network security alerts and investigate them using actual data. These labs are designed to challenge you and force you to think through the process of building an intrusion timeline and asking the right questions.
- Participation in our student charitable profit sharing program. A few times a year we designate a portion of our proceeds for charitable causes. AND students get to take part in nominating charities that are important to them to receive these donations.
- 6 months access to course video lectures and lab exercises with the Investigation Ninja tool. You can extend access later if you need more time.
- Access to Chris Sanders online “office hours” held periodically
- A Certification of Completion
- 30 Continuing Education Credits (CPEs/CEUs)
Register Now for Just $647
This course is also offered as a two-day on-site class taught at your organization. This includes access to the online course material for all attendees. Contact Us for On-Site Inquiries (2-Day Course + Online Access)
Bulk discounts are available for organizations that want to purchase multiple licenses for this Investigation Theory training course. Please contact us to discuss payment and pricing.
You can view student testimonials here.