Late last year I wrote a blog post focused what I have perceived as a coming evolution of focus for security investigations. This evolution will push us into an era where the human analyst takes center stage in a security investigation, and where tools and processes will shift to augment human cognitive ability. In this article, I want to expand on some of those thoughts and describe my research on how human analysts solve investigations. This is summarized as a concept I refer to as visual investigative theory.
I want to begin by revisiting the KSU ethnographic study I called out in a previous article. When several KSU sociologists spent time performing an ethnographic study of a security operations center they had some very interesting findings. Based on those findings, I drew the following conclusions:
Investigative process knowledge is tacit. While experienced analysts have the ability to quickly solve investigations, they almost never have the ability to accurately describe what makes them so effective.
Fundamental skills and domains aren’t well established. We have an inability to identify the fundamental cognitive (not platform or technology specific) skills that are required to successfully detect and response to compromises. Further, we have not clearly identified subdomains of the broader security investigation domain, and differentiated the cognitive skills necessary to define and excel at each of them.
Knowledge transfer is limited. Without identified skills and domains, or adequate explicit process knowledge, our ability to train less experienced analysts is hampered. Most SOC’s rely exclusively on “over the shoulder” training where less experienced investigators simply watch experienced investigators work. While this has its place, a training program founded exclusively in this type of instruction is fundamentally flawed and lacks proper fundamental building blocks.
Investigations rely on intuition. The aforementioned findings lead to the conclusion that the investigative process relies heavily on intuition. Beyond tool and technology specific processes, investigators rely almost exclusively on what they might refer to as “gut feeling” to determine which steps they should take to connect the dots and solve the investigation at hand.
Examining Intuition
Intuition typically refers to the ability to understand something immediately without the need for conscious reasoning. The concept of intuition isn’t new, but its acceptance in the world of psychological research is. Psychology itself is a fairly young field, having only existed since the late 1800s and becoming exponentially more popular around the mid 1900s. Most founding fathers of psychology dismissed intuition. Even Sigmund Freud was famous for saying that “it is an illusion to expect anything from intuition.” However, that has changed in recent years with the development of more sophisticated brain imaging techniques.
If you’ve ever had a head injury where you’ve scrambled your eggs a bit, then there is a chance that you’ve been the beneficiary of an MRI scan. A newer and more advanced form of this is something called an fMRI scan, which allows doctors and researchers to measure the response level from certain areas of the brain when specific stimuli are introduced.
A group of researchers recently wanted to better understand the science behind intuition. To do this, they utilized fMRI technology to measure the response of different areas of the brain while presenting chess of varying degrees of expertise with match scenarios designed to draw upon their sense of intuition. While chess is very different from investigating security incidents, participants in each of these tasks claim to be successful thanks in part to unexplainable, tacit intuition.
In this scenario, researches selected two groups of chess players. The first group consisted of journeyman chess players who were familiar with the game, but would not be considered professionals or experts. The second group consisted of professional chess players with high global rankings. Both groups were presented with an image of a chessboard showing a game in progress for a short period of time. They were then asked questions relating to what moves they thought would be best next, while their neural response was measured using fMRI technology.
The results of this experiment were exciting because they identified a specific area of the brain where the chess experts showed significantly more activity than the inexperienced players. This area, called the precuneus, showed 2.1x more activity in the chess experts. This indicates that there is a biological basis for the unconscious thought that we’ve previously only been able to refer to as intuition. Because of this, many psychologists have begun to shift their beliefs such that they recognize the existence of intuition.
Figure 1: The precuneus is related to what we think of as intuition
This gets really interesting when you consider that the precuneus is also known to be responsible for portions of our working memory, and our capacity to form and manipulate mental images. Before we dive into that, let’s have a quick primer on how human memory works.
Modeling Memory
There are multiple theories and models related to how memory is organized, but the most widely accepted model breaks it down into three distinct categories.
Sensory Information Store (SIS) is the most volatile form of memory, and is associated with the lingering sensations that follow a stimulus. For instance, if you are starting at an object and close your eyes, you may still “see” the object for a brief period as though its printed on to the inside of your eyelids. This is an example of SIS.
Short-term Memory (STM) is volatile memory that exists in conscious thought. When you are actively thinking about something, you are using STM to do so. This is why STM is often referred to as working memory (WM). Things that we perceive and only contemplate for a short period of time that aren’t worthy of storing permanently are processed by STM. In computing terms, STM is akin to RAM.
Long-term Memory (LTM) is our most resilient form of memory. Once something gets encoded into LTM it is stored for a very long time. For input into LTM, some theorize that we only encode certain things into LTM while others propose that we encode most everything. For output from LTM, some propose that we store everything but simply can’t recall it all, while others propose that some things that are encoded eventually decay out over time. In computer terms, LTM is similar to the concept of disk storage.
For the purposes of this article, we are most concerned with short term / working memory. As with memory in general, there are multiple models for how STM is organized, but one of the most widely accepted is Baddeley’s Model of Working Memory.
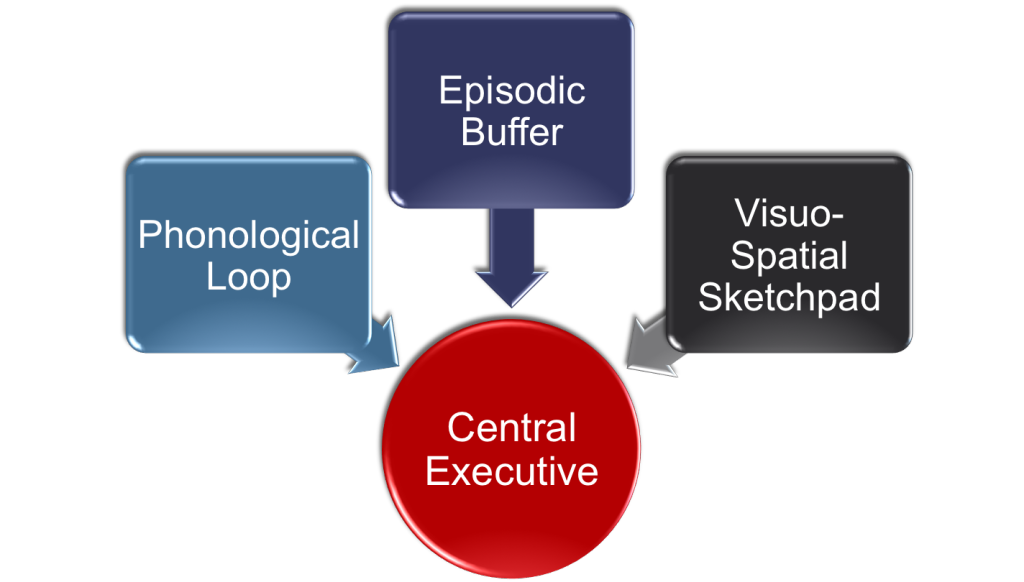
Figure 2: Badelley’s model of working memory
In Badelley’s model, there are three components of WM that are all controlled by a central executive services.
The Phonological Loop stores audible information and prevents it from decaying by continuously repeating its contents. For example, it allows you to use working memory to remember a phone number by repeating it over and over again in your head.
The Episodic Buffer holds representations that integrate multiple types of information to form a single unified representation of memory. It was a more later and more recent addition to the model.
The Visuospatial Sketchpad (VSSP) allows us to mentally picture and manipulate visual information about objects. For example, if you picture a multi-colored cube rotating so that different colors face you as time advances, you are using the VSSP. It is this portion of working memory we are most concerned about for the purpose of this discussion.
Visual Investigative Hypothesis
We can apply what we just learned about working memory to the earlier discussion about intuition. As we discovered, intuition is strong related to the precuneus. Examination of other psychology and neurology research tells us that the precuneus is involved in several different things, including (surprise!) working memory and visuospatial processing. While not definitive, this does lead us to believe that the visuospatial sketchpad and the mental visualization and manipulation of objects may be related to intuition and how humans solve complex problems.
Of course, I’m not a neuroscientist and there is still quite a bit of ongoing research here. However, I think there are many cases when this theory makes sense. For example, prolific and prodigal musicians have been known to say that they can literally “see” the music as they are composing or playing it. Individuals who practice stock trading will also speak about how they can see trends forming before they actually happen, allowing them to execute smart orders and make a sizable profit. Even going back to our earlier discussion of chess, expert chess players will state that a reason they excel at competition is their ability to “see” the board and picture future situations better than their opponents.
It would truly appear that humans excel at processing information when it’s possible for them to visualize it, so why wouldn’t the same apply to security investigations? I’ve been an analyst myself for quite some time, and I’ve also had the pleasure of working with and speaking to a lot of other analysts, and I think this does apply. It’s important to realize that in a lot of cases, people may visualize things like this subconsciously without actually realizing that they are solving problems visually. I believe that individuals who excel at solving information security investigations also solve problems visually. In fact, I think that many subconsciously see a data or attackers moving thorough a network as they assimilate various data points from system logs, packet captures, and IDS alerts. I’ve summed this theory up into something I call visual investigative hypothesis.
In short, the visual investigative hypothesis states that security analysts are more efficient, and more likely to arrive at a conclusion based on an accurate representation of events that occurred when they are able to visualize the relationships that represent a network compromise and build a mental picture of an attacker moving through a network.
In psychology, most principals exist as either hypothesis or theories because our understanding of the brain, while advancing, is still very limited. Many highly probable concepts and others considerably less probable will likely never advance to being considered confirmed truths, so while I do expect to mold my research into a more sound theory, I certainly don’t expect to ever definitively and quantifiably prove it as a ground truth. A great deal of my doctoral coursework will be geared towards development of visual investigative hypothesis into more formal theory, which will involve continued efforts interviewing security analyst and conducting case studies regarding their investigative habits, failures, and successes.
Maximizing Working Memory Effectiveness
While there is still much work to do, if you subscribe to the visual investigative hypothesis there are a few ways you can begin shifting your investigative technique towards something that is much more visual. When considering working memory, its important to understand that it is a finite resource. Humans only have so much capacity in working memory, just like computers have only so much RAM. Some people have a larger WM capacity while some have less. In addition, external factors like tiredness and stress can negatively affect the situational capacity of WM. Knowing WM is a finite resource can guide us towards ideas for optimizing our investigative habits and the tools we use to perform our work.
As an example, consider the magic number seven, a theory developed by Princeton psychologist George Miller. This theory states that an average person can hold seven objects in working memory, plus or minus two. This means that if I were to list twenty random objects, you are likely to only remember five to nine of them. This is the result of biology, and most likely something that can’t really be changed person to person.
This applies to the investigative process when you think about all of the various pieces of information that an analyst has to store in WM when attempting to describe an anomalous event or breach. At any given point an analyst might need to consider a pair of IP addresses, a port number, protocol, two system roles, a detection signature, a file name, a portion of a file hash, a system name, a start time, and an end time. No wonder investigations push the limits of WM capacity.
Overcoming magic number seven and limitations of working memory is all about making the right information available at the right time, and in the right way. Some ways that we can do this during an investigation include:
Data Scoping: Analyst should only retrieve the information they need for the time duration required. Have too little data is a bad thing, but having too much data can be just as bad. This can be achieved by formulating concise questions before seeking data, and making sure your data sources can be queried flexibly.
Focusing on Relationships: Humans remember things better if they can associate them with existing schemas in long-term memory. If I were to tell you ten random objects and ask you to recall them an hour later, you would have trouble doing so. If I repeated the same experiment with related items like breakfast foods, your recall would be much better. We can force objects in an investigation into similar schemas by describing entities as nouns and their interactions as verb, building graph/link representations that help us conceptualize a potential attackers movement through a network this way. One of the bigger gaps between network attackers and defenders is that attackers often think in this type of relationship-centric manner, and defenders don’t.
Rethinking Search: Searching through data itself should be less of an iterative process of querying a data source, viewing a response, and repeating. It should be more of an exploration where the analyst anchors themselves to a point in the data and they explore outward from there. This supports a relationship-centric view of security.
Visualizing Events over Time: The activities of a suspected adversary typically lend themselves well to groupings of major and minor events occurring at specific times. Using timelines to represent these groupings of events with pointers back to the source data can provide a visual construct that is useful for easing pressure on WM.
Easy to Remember Names: Long strings of characters like MD5/SHA1 hashes or even IP addresses take up valuable space in WM. Often times analysts will try to remember sections of these objects just as the last octet of an IP address or the last few characters of a file has. Another strategy here is to assign common names to various unique hosts and files for quick reference during the investigation. I’ve done this with animals or food in the past. Thus, f527fe6879ae8bf31cbb1e5c32d0fc33 becomes Fennel, and 123.1.2.3 becomes Puma. This is made easier when the tools used facilitate it. Of course, protocols like DNS can make this easier too, but its important to remember that a DNS name simply represents a point to a host, and not a host in itself.
Conclusion
The concepts surrounding the visual investigative hypothesis aren’t new. Most of us know that the right visualizations can help us find evil better, but beyond that we don’t collectively have a lot of solid science that we can use to apply it to security investigations or how we train analysts. While I think there are some practical takeaways we can draw from this immediately, there is still much work to be done. I’m looking forward to continuing my research here and applying cognitive psychology concepts to the security investigation process.

1 thought