*** Dec 30th Update — Thank you to everyone who donated or partnered with us…
Last September I released my latest book, Intrusion Detection Honeypots: Detection through Deception. Today, I’m announcing…
I’m looking for the right person to join me full time at Applied Network Defense.…
Each December, I like to reflect on the best things I’ve read over the course…
I’m thrilled to announce the release of my newest book, Intrusion Detection Honeypots: Detection through…
In an essay I published earlier today, I spoke about the recurring debate in information…
Should security researchers release offensive security tools (OSTs)? Industry insiders and outsiders have debated the…
Most cyber security educators are practitioners first and educators second. While this model ensures learners…
Each December I like to reflect on the best things I’ve read over the course…
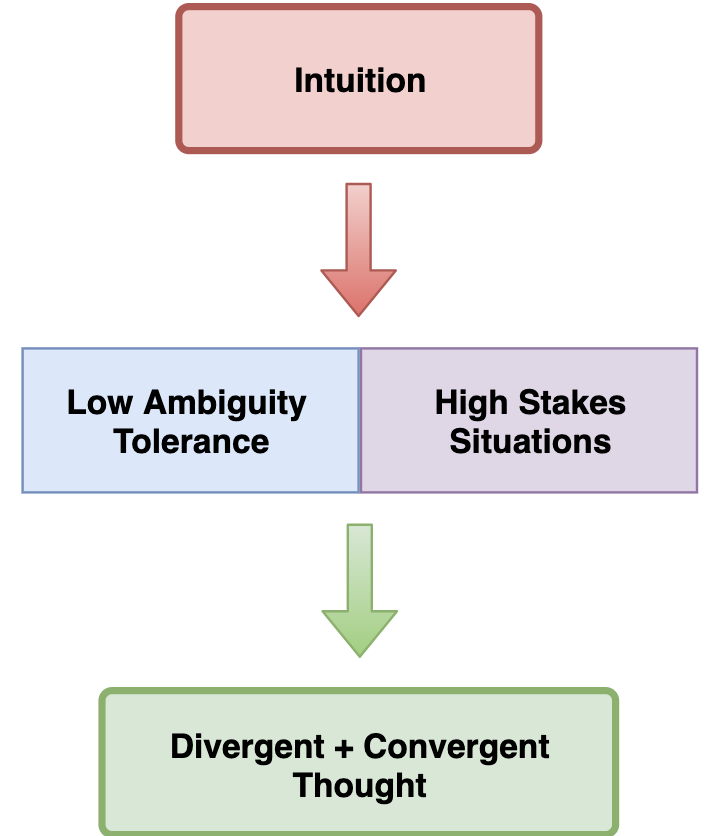
Creative Choices: Developing a Theory of Divergence, Convergence, and Intuition in Security Analysts
Humans lie at the heart of security investigations, but there is an insufficient amount of…